
Account / Influencer Team
Identify right-fit creators and influencers, gain approvals, execute campaigns, oversee content and deliver accurate, time-saving results.
We’ve established a robust information security management system to guard our security measures. Adhering to industry best practices, we protect our valuable assets and integrate seamlessly with our risk management strategy. Our clear objectives and principles ensure strict measures to safeguard our organization.

Shelby Currie, Paid Social Strategist, Moroch
Literally changed our influencer approach for local and helped us differentiate. The best part of Tagger is the automated reporting. No longer are we manually tracking and logging into Instagram on our phones to check things, we're able to track in such a smarter way. I also love the search parameters! They made us able to actually source influencers locally and differentiate ourselves in the market with our client offerings.
Data Compliance
Tagger prioritizes ethical data practices, securing API approval from social media platforms and respecting data laws and user privacy. Adherence to legal requirements and social media platform terms, guided by our Code of Conduct and Ethics, ensures integrity. This ethical foundation is essential for successful influencer marketing campaigns, respecting user privacy and legal boundaries.
Privacy Compliance
We fully comply with privacy laws, regulations and best practices. We are GDPR, CCPA, UK Data Protection Act 2018 and COPPA compliant.
Cyber Security
We use advanced security controls like WAP, NGFW, SIEM, systems, networks, infrastructure monitoring tools, DMZ and vulnerability scanners. Our system uses a hardened and patched OS, applications and DB. We review vulnerability bulletins continuously and have solutions to mitigate DOS and DDoS attacks. We perform penetration tests annually.
Disaster Recovery & Business Continuity
We maintain disaster recovery and business continuity plans as part of our Information Security and Privacy Management System. We have high availability infrastructure in the US and backup failover to another US region. We regularly test and refine this plan to ensure the fastest recovery during a disaster.
Responsible Disclosure
If you find a security vulnerability on Tagger services, please contact us immediately. We take security concerns seriously and will work to resolve any issues responsibly. To report a vulnerability, please email us at [email protected]
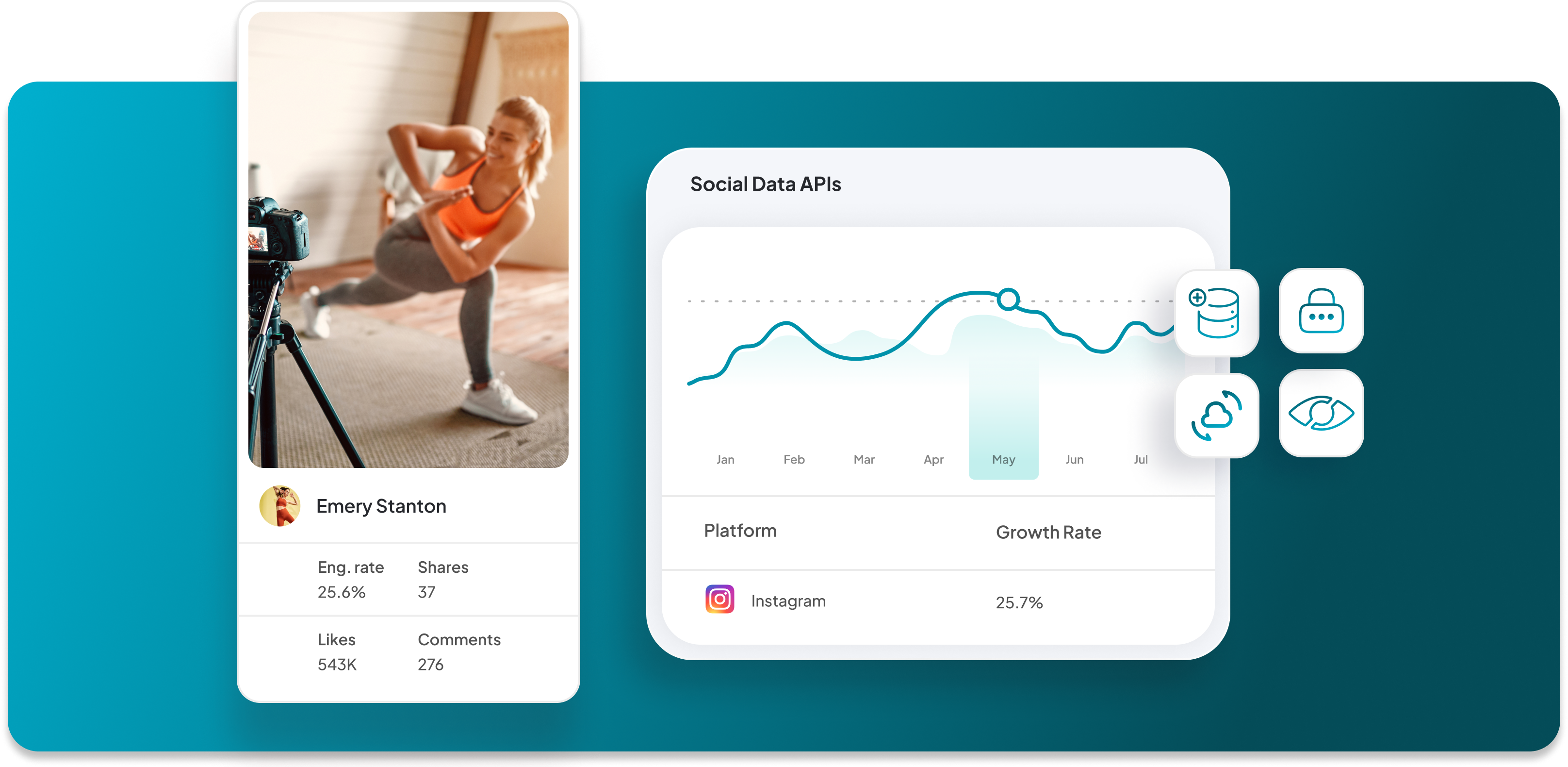

Identify right-fit creators and influencers, gain approvals, execute campaigns, oversee content and deliver accurate, time-saving results.

Formulate strategies with precise audience targeting, influencer insights, strategy development, performance measurement and data-informed decision-making.

Measure success with robust data sources, simplified insights, flexible data visualization, real-time reporting, and actionable insights for informed decision-making.
Where influencer marketing + social intelligence meet.
Let’s get started.